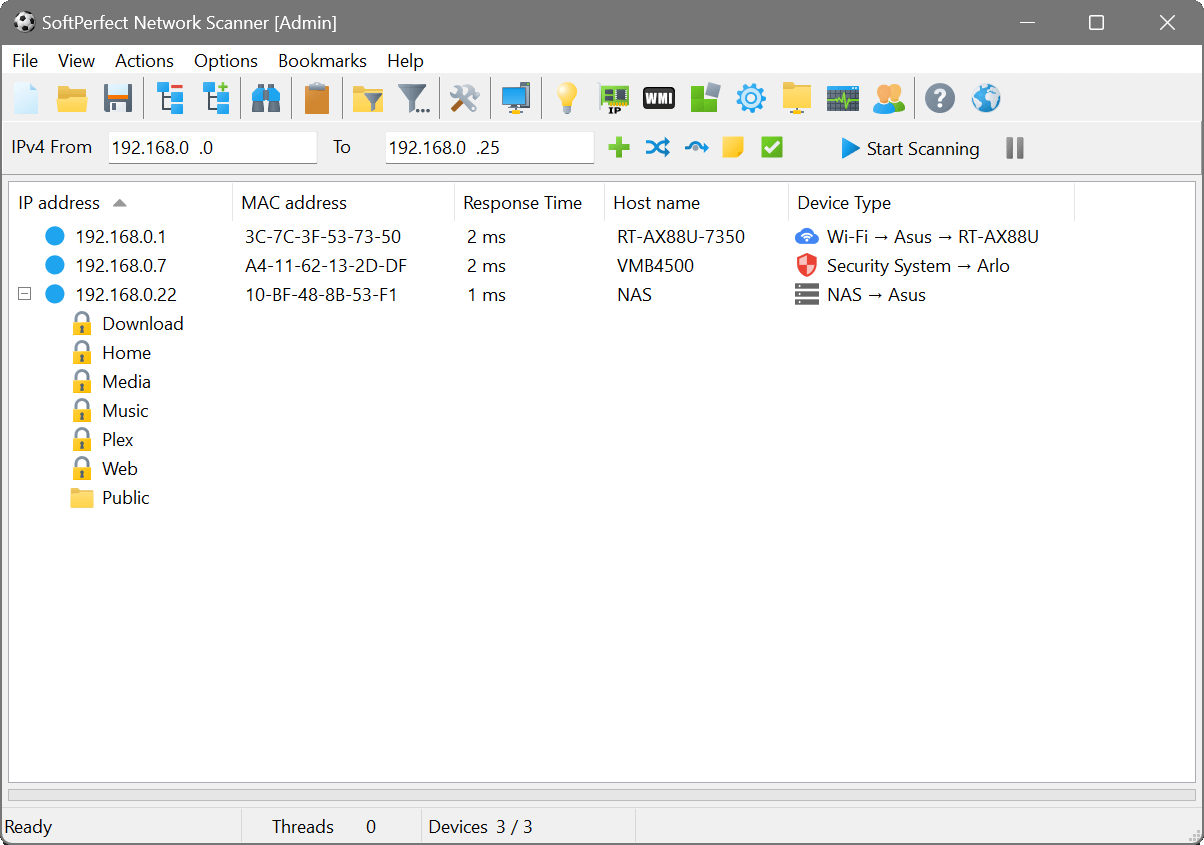
Option Scanning Tools For Network
We use cookies to personalize content and ads, and to analyze our traffic. We also share information about your use of our site with our social media, advertising and analytics partners who may combine it with other information that you’ve provided to them or that they’ve collected from your use of their services. Use the remote network scanner to find all connected devices on a network. With the advanced Network scanning tool for windows and mac. The Free IP Network Scanning Tool. The free IP network scanning tool scans IP addresses in any range as well as any of their ports to retrieve detailed information.
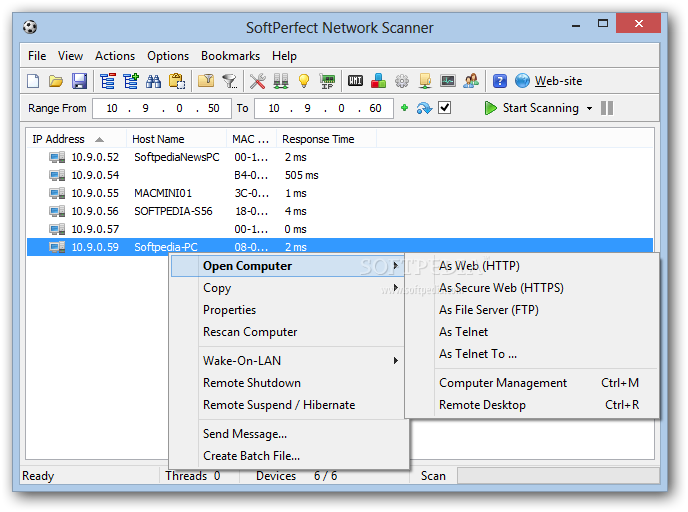
What network scanning tools have a stealth option to avoid detection?
Rory Alsop♦4 Answers
As with most things - it isn't about the tool, it is how you use it.
Take nmap for example.
Beginners to the tool or script kiddies might run scan using the default option.
nmap 192.168.1.0/24
The default behavior for nmap without specifying any addition flags would be to perform a syn scan, so the above query would be equal to.
nmap -sS 192.168.1.0/24
Syn scans are reasonably stealthy. However, most modern firewalls/IDS should be able to detect syn packets as it is a very common scan technique.
Slightly better but still inexperienced users might perform even noiser scans using nmap.
nmap -sV 192.168.1.0/24
nmap -A 192.168.1.0/24
An nmap scan triggered with those two scan flags are VERY noisy. In addition to sending a variety of packet types and grabbing banner information, nmap will use the nmap scripting engine to perform additional tasks such as bruteforcing the SNMP community string if applicable. Such scans will be easily detected.
More experienced users can perform more stealthy scan types by specifying certain flags. nmap is a very powerful tool as it allows you to set different flags in a TCP packet to evade firewall rules. ACK & FIN are two very commonly used techniques to evade firewalls.
Other advanced techniques like idle scan can also be performed using nmap. It is a very versatile network scanner that can be very silent in the hands of an advanced user.
Some tips
Do not perform syn scans or version scans on entire subnets unless needed. It is slow and noisy. Instead, use the ping scan option to find out which hosts are active on a subnet.
nmap -sn 192.168.1.0/24
This option would return a list of active host IP and MAC addresses in the subnet.
Once you have obtained a list of active hosts, selectively scan hosts which you think are interesting. For example, the IP address 192.168.1.1 seems interesting to me, I might want to know more about it. Perform a syn scan.
nmap -sS 192.168.1.1
By default, nmap scans for the most popular thousand or so ports according to a list compiled by the author. This is good enough for most purposes. However, there might be some scenarios where you might want to specify specific ports. You can do that using the -p flag.
nmap -sS -p 80 192.168.1.0/24
This scan would send syn packets to the entire subnet, searching for active IP addresses with port 80 open. This is a useful scan for determining which host might have an active HTTP server.
nmap -sV 192.168.1.1
The -sV flag specifies the version scan option. This option instructs nmap to send a wide variety of packets to the hosts and scanning the headers of the packets returned to check for the exact version of a service the host is running.
This is a very powerful but noisy version. Use with caution.
nmap -A 192.168.1.1
Network Scanning Tools Free
The -A flag instructs nmap to use an aggressive scan. This is one step up from the version scan and utilizes the nmap scripting engine. This is very noisy.
nmap is a highly powerful tool. Xprotect essentials download. If you want to learn more, i highly suggest you pick up the book written by its author.
.gif) D.W.
D.W.I'd actually say that the best way to avoid detection from IDS is not to use scanners at all. Most scanning tools have signatures which can be recognised by IDS, so can be incorporated into their rulebases. Some (like nmap) have options to slow down the scan or scan in a more random fashion to try and avoid detection, but whether IDS trips here will depend on how it's configured.
There are two types of traffic which I'd expect to bypass IDS.
- Legitimate traffic - For example connections to ports 80/443 on a web server. if you're looking at an external network then trying to manually connect to systems on web ports is unlikely to trip IDS unless you try to do it a lot very quickly.
- Obvious Junk Traffic - Again on external networks, to avoid getting overwhelmed with false positives, the IDS might be tuned to discard specific scan types (e.g. scans for port 445/TCP) . Whilst those aren't likely to be successful, you could use a scan for that port to try and establish live hosts in a range and you might bypass the IDS as it'll be taken as one of the usual scans that every system on the Internet gets.
She can use standard, non-intrusive scanners like Nmap. It should be adjusted the way that it's slow enough to not trigger alarms. The information gathered is:
- Active hosts
- Operating system version
- Running services (ports)
- Banners / versions of these services
Also, you can perform non-invasive Nessus scan, the way that it's not trying to run exploits or authenticate, but just pings, connects to ports and check banners. The key elements:
- Slow scan, maybe from multiple ip numbers
- Do not attempt to login, but just read the banner
In the easiest scenario, is discovering their subnet, and then visiting via the browser each host. It has high efficiency and cause little alarming.
Scanning Options For Windows 10
You could use nmap with tortunnel and proxychains. But scanning through tor is very, very slow.
And remember to create a rule that drops packets form your real ip so your real IP address is not disclosed.
(if your are on linux iptables -A OUTPUT --dest 'target' -j DROP)